
Explaining Phishing and Phishing as a Service (PhaaS).
Phishing is a common hack that aims to trick people into revealing private information, including credit card numbers, passwords, and personal identities.
A staggering 300,497 phishing cases were reported to the US FBI in 2022 alone. These attacks resulted in victims losing more than $52 million. This usually involves sending fake emails that appear genuine, tricking recipients into opening malicious links or requesting sensitive information. Phishing as a Service (PhaaS) is a worrying development in the world of cybercrime.
By using a subscription-based web service called PhaaS, even non-technical criminals can easily carry out sophisticated phishing attacks. These companies offer pre-built phishing kits, editable templates, and server infrastructure to create fake web pages.
For example, a cybercriminal might sign up for a PhaaS platform, create an email template that looks like it comes from a respected cryptocurrency exchange, and distribute it to thousands of potential recipients. A link to a fake login page intended to steal users’ credentials may be included in the email.
Cybercriminals may quickly launch large-scale phishing campaigns using PhaaS, posing a greater threat to both individuals and businesses. The accessibility of PhaaS lowers the barrier of entry for cybercrime, a major concern for Internet consumers and cybersecurity experts globally.
How PhaaS works
PhaaS makes it easier for fraudsters to launch phishing attacks by giving them access to comprehensive toolkits and infrastructure.
It works as follows:
PhaaS groups
Pre-packaged phishing kits containing all the tools, infrastructure, and templates needed to perform phishing attacks are available from PhaaS vendors. Email templates, mock login pages, domain registration services, and hosting infrastructure are included in these packages.
Customization
The degree of customization offered by different PhaaS systems varies. Phishing emails, websites, and domains may be altered by scammers to appear authentic and trustworthy. Phishing campaigns can be customized to target specific people, companies, or sectors.
Targeting
Phishing attacks made possible by PhaaS are becoming more sophisticated. Cybercriminals have the ability to design highly targeted advertising campaigns that mimic the branding and communication strategies of reputable companies and their offerings. Attackers can create convincing communications that have a greater chance of deceiving recipients by using personal information derived from social media, data breaches, and other sources.
For example, attackers often pretend to be support staff from popular wallets, exchanges, or projects on social media (Telegram, Discord, Twitter, etc.). They offer assistance and trick users through false claims of gifts, airdrops into giving away private keys or seed phrases, or establishing connections with compromised wallets to withdraw their funds.
PhaaS risks
PhaaS has significantly lowered the barrier to entry for hackers, resulting in a significant increase in the amount and sophistication of phishing attempts.
Even those with no technical experience can simply launch complex phishing attacks with PhaaS using the pre-packaged toolkits, customizable templates, and hosting infrastructure offered by PhaaS providers.
The potential for significant financial loss is the main risk associated with PhaaS. The goal of phishing scams is to obtain users’ private keys, seed phrases, or login credentials. They can be used to access their accounts and drain their cryptocurrency wallets for nefarious purposes. For example, attackers changed the front-end of BadgerDAO in 2021 after tricking users into providing permissions that allowed their funds to be drained.
PhaaS attacks have the potential to undermine trust in the cryptocurrency community. Successful scams can discourage people from using reputable projects and services, preventing their widespread adoption. These attacks are especially vulnerable to novice cryptocurrency users. They can be more likely to fall into the trap of social media impersonations or websites that look authentic due to their lack of experience.
Phishing attacks are becoming more sophisticated; They often use social engineering strategies and imitate real platforms. This makes it difficult for even experienced users to recognize them.
PhaaS isn’t just limited to large-scale email campaigns. Phishing attacks are directed at well-known people or companies in the cryptocurrency industry. Such attacks use personal information to trick certain individuals or organizations into giving up sensitive data or taking actions that result in financial loss or security breaches.
How to defend against PhaaS
The ideal way to protect against PhaaS is to practice constant vigilance: double-check everything (URLs and sender addresses), never click on spammy links, and never share your private keys or seed phrases.
Multi-layered security approach and technical defenses
Install firewalls, network monitoring tools, endpoint security, and powerful email filtering. These technological safeguards help identify and block dangerous attachments, phishing emails, and suspicious network activity.
User awareness training
Regularly teach employees how to spot and report phishing attempts. Tell them the typical signs of phishing attempts. This entails telling people to closely examine sender addresses, determine the urgency of messages, stay away from questionable links, and stop sending private information via email.
Security policies
Implement security measures such as best practices for passwords and two-factor authentication (2FA). To avoid unwanted access, encourage the use of strong, unique passwords that are updated regularly.
Implement DMARC
To help remove fake emails, use email authentication methods such as Domain-Based Message Authentication, Reporting, and Conformance (DMARC). By helping to verify email authenticity, DMARC reduces the success rate of phishing attempts.
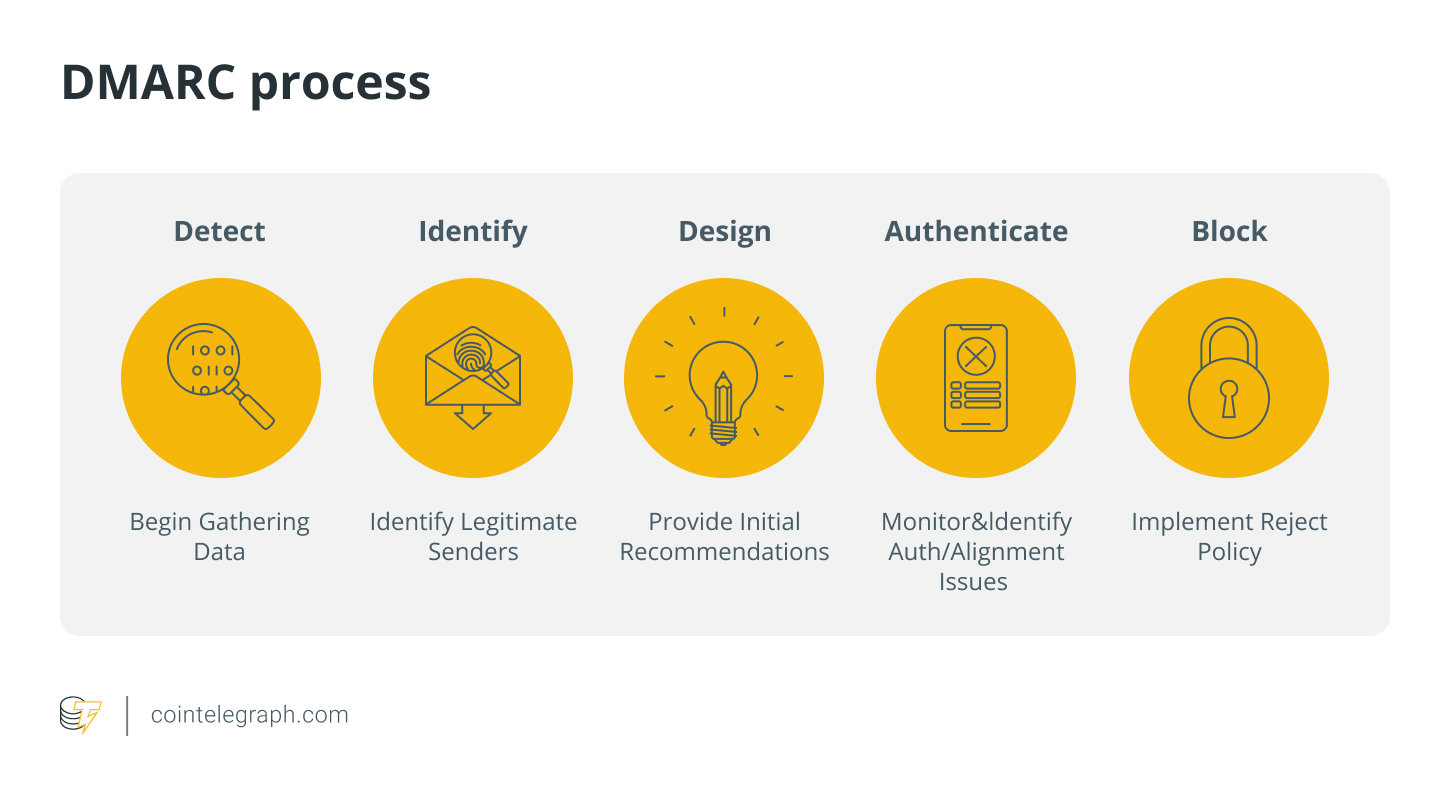
It gives domain owners insights into their domain’s email authentication statistics and lets them set policies for handling unauthenticated emails.
Threat intelligence
Sign up for threat intelligence services to receive information about the latest phishing attacks and PhaaS technologies. To better defend cryptocurrency platforms against evolving cyber threats, keep up with new developments in cyber attacks and emerging online risks.