
Infinite Mint Attack Explained
An infinite coin attack occurs when an attacker manipulates contract code to continuously mint new coins beyond the allowed supply limit.
This type of hack is most common in decentralized finance (DeFi) protocols. The attack threatens the integrity and value of the cryptocurrency or token by creating an infinite supply of them.
For example, a hacker exploited a smart contract vulnerability in the Paid network to create and burn tokens, resulting in a loss of $180 million and an 85% drop in the value of the PAID. More than 2.5 million paid tokens were converted to Ethereum (ETH) before the attack was stopped. The network compensated users, dispelling rumors of an inside job (rug pulling).
A malicious actor can take advantage of such attacks by selling illegally generated tokens or interfering with the regular operations of the affected blockchain network. The prevalence of endless Mint attacks highlights how important it is to conduct thorough code audits and integrate security measures into smart contract development to protect against exploits of this type.
How does Mint Infinite Attack work?
To create a vulnerability that allows an attacker to create an infinite number of tokens, the Infinite Mint attack targets smart contract vulnerabilities, particularly those related to cryptocurrency minting functions.
Step 1: Identify weaknesses
The attack methodology involves identifying logical vulnerabilities in nodes, usually related to input validation or access control mechanisms. Once the vulnerability is found, the attacker creates a transaction that takes advantage of it, forcing nodes to create new tokens without the necessary authorization or verification. This vulnerability could make it possible to bypass planned limitations on the number of tokens that can be created.
Second stage: exploitation
The vulnerability is triggered by a malicious transaction created by the attacker. This might involve changing settings, implementing certain functions, or taking advantage of unexpected connections between different code segments.
Step 3: Unlimited Mining and Token Dumping
This exploit allows the attacker to emit codes that go beyond what the protocol architecture provides. This flood of tokens can cause inflation, which can reduce the value of the currency associated with the tokens and lead to losses for various stakeholders, including investors and users.
Token flooding is the practice where an attacker quickly floods the market with newly created tokens and then exchanges them for stablecoins or other cryptocurrencies. The value of the original token is greatly diminished by this unexpected increase in supply, causing prices to collapse. However, selling inflated tokens before the market has a chance to benefit the attacker.
Consequences of the Infinite Mint attack
An Infinite Mint attack leads to a rapid decline in token value, financial losses, and ecosystem disruption.
An Infinite Mint attack creates an infinite amount of tokens or cryptocurrencies, instantly depreciating the value of the affected assets and causing significant losses for users and investors. This endangers the integrity of the entire ecosystem by undermining trust in the relevant blockchain network and its associated decentralized applications.
Additionally, by selling inflated tokens before the market fully reacts, an attacker can profit and potentially leave others holding worthless assets. As a result, investors may find it difficult or impossible to sell their assets at a fair price if the attack causes a liquidity crisis.
For example, during the Cover Protocol attack in December 2020, the value of the token fell from over $700 to less than $5 within hours, and investors who held COVER tokens suffered financial losses. Pirates minted more than 40 quintillion coins.
A collapse in the value of a token could disrupt the entire ecosystem, including decentralized applications (DApps), exchanges, and other services that depend on the stability of the token. The attack could lead to legal issues and regulatory review of the project, which could lead to fines or other sanctions.
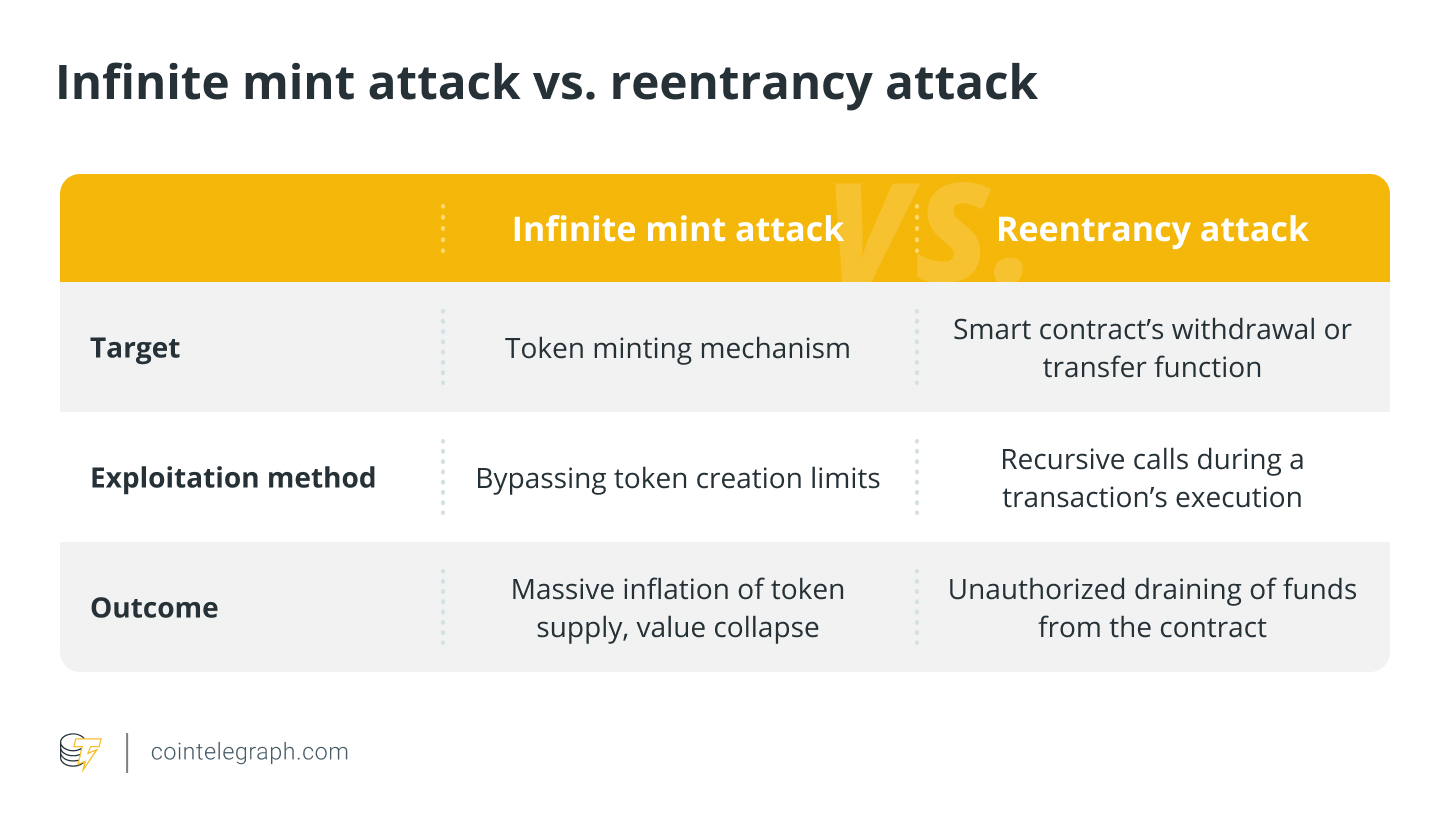
Infinite Mint Attack vs. Reentry Attack
An Infinite Mint attack aims to generate an unlimited number of tokens, while a re-entry attack uses withdrawal mechanisms to continually drain funds.
Infinite Mint attacks take advantage of flaws in the token creation process to generate an unlimited supply, leading to a decline in value and losses for investors.
Reentry attacks, on the other hand, focus on withdrawal actions, giving attackers the ability to continually drain funds from a contract before the contract has a chance to update its balances.
Although any attack can have catastrophic consequences, it is essential to understand the differences in order to develop effective mitigation techniques.
The main differences between an infinite mint attack and a reentry attack are:
How to Prevent Infinite Mint Attacks in Crypto
Cryptocurrency projects can significantly reduce the risk of becoming the target of endless attack and protect community members’ investments by focusing on security and adopting preventive measures.
It needs a multi-faceted strategy that prioritizes security at every stage of a cryptocurrency project to avoid endless attacks. There is a need for thorough and frequent audits of smart contracts by independent security experts. These audits carefully examine the code for flaws that could be used to mint untold amounts of money.
There must be strict access controls; The power to mint currency should only be granted to authorized parties; Multi-signature wallets should be used to increase security. Real-time monitoring tools are essential to quickly respond to potential attacks and identify any strange transaction patterns or sudden increases in token supply.
Projects should also have robust backup plans in place to quickly manage any potential attacks and minimize damage. This involves having open lines of communication with exchanges, wallet providers and the community at large to anticipate potential issues and plan solutions.